The Introduction of ZIP Domains Raises Cybersecurity Concerns
- Google’s introduction of ZIP and MOV Internet domains, which are also common file extensions, has sparked concerns among cybersecurity experts. They warn these domains could be exploited by threat actors for phishing attacks and malware delivery, as some online platforms and messaging services may automatically convert file names with .zip and .mov extensions into URLs.
- The debate about the potential risks of these new domains is ongoing in the developer and cybersecurity communities. While some believe the fears are unwarranted, others argue that these domains could add unnecessary risk to an already volatile cybersecurity environment. Several individuals have started using .zip domains to educate users about the associated risks.
Cybersecurity researchers and IT administrators have voiced concerns over Google’s newly introduced ZIP and MOV Internet domains. These domains, they caution, could potentially be exploited by cybercriminals for phishing attacks and malware delivery. The issue lies in the fact that these domains are also extensions of files commonly shared in online discussions, messages, and forum posts. Consequently, these file extensions could now be automatically converted into URLs by some online platforms or applications.

The Problem with ZIP and MOV Domains
Online, you often encounter two frequently used file formats: ZIP archives and MPEG 4 videos. These file types are typically identified by their respective file extensions, namely .zip and .mov. However, due to recent developments where these extensions have become top-level domains (TLDs), specific messaging platforms and social media sites might automatically transform file names with .zip and .mov extensions into URLs.
The implications of this are potentially concerning. For instance, on platforms like Twitter, if someone sends instructions about opening a ZIP file or accessing a MOV file, the file names could be automatically transformed into URLs. This could create a situation where a user might click on a link thinking it would lead to a file download, when in reality, it could lead to a phishing scam or a site delivering malware, particularly if the domain is owned by a malicious actor.
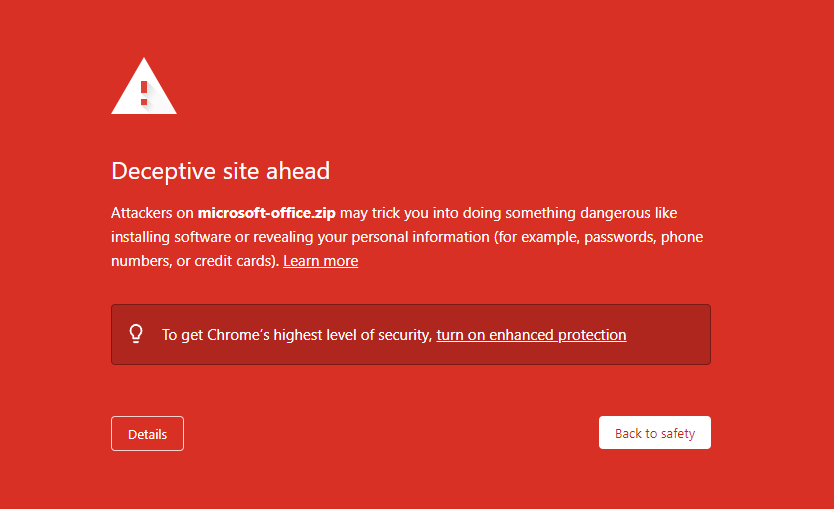
The risk of abuse associated with these domains is not merely hypothetical. According to Silent Push Labs, a cybersecurity intelligence firm, they recently uncovered a suspicious phishing page at microsoft-office[.]zip. The page appeared to be designed with the intention of tricking users into disclosing their Microsoft Account credentials. Furthermore, research indicates that malicious actors have the potential to create deceptive phishing URLs by utilizing Unicode characters and the userinfo delimiter (@) within URLs, making them more convincing and deceptive. These URLs could appear to be legitimate file download links but would, in reality, redirect users to deceptive websites.
Diverse Opinions Spark Debate
The introduction of ZIP and MOV TLDs has ignited a debate among developers, security researchers, and IT administrators. Opinions are divided, with some feeling that the concerns are unwarranted, while others believe that these new TLDs introduce unnecessary risk to an environment already fraught with cyber threats.
It is worth noting that a notable trend has emerged where certain individuals are registering .zip domains that align with frequently encountered ZIP archives, like update.zip and backup.zip. These domains are being used to display information about the risks associated with ZIP domains, among other benign information.
Mozilla’s Public Suffix List (PSL), which encompasses all public top-level domains, faced a request from open-source developer Matt Holt to eliminate the ZIP TLD. The PSL community, on the other hand, clarified that despite the associated risks, these TLDs remain valid and should not be excluded from the PSL. Removing them could have unintended consequences for the functionality of legitimate websites, as stated by the PSL community.
As this debate continues, the cybersecurity community will be closely watching how these new TLDs are utilized and what potential security implications may arise. The situation underscores the constant evolution of the cybersecurity landscape and the importance of ongoing vigilance and adaptation.





